
Protect your assets
with our Expert –
Managed Security Services
Our Managed Security Services
Stay ahead of cyber threats with our Managed Security Services, providing 24/7 monitoring and protection for your digital assets
Why It’s Important

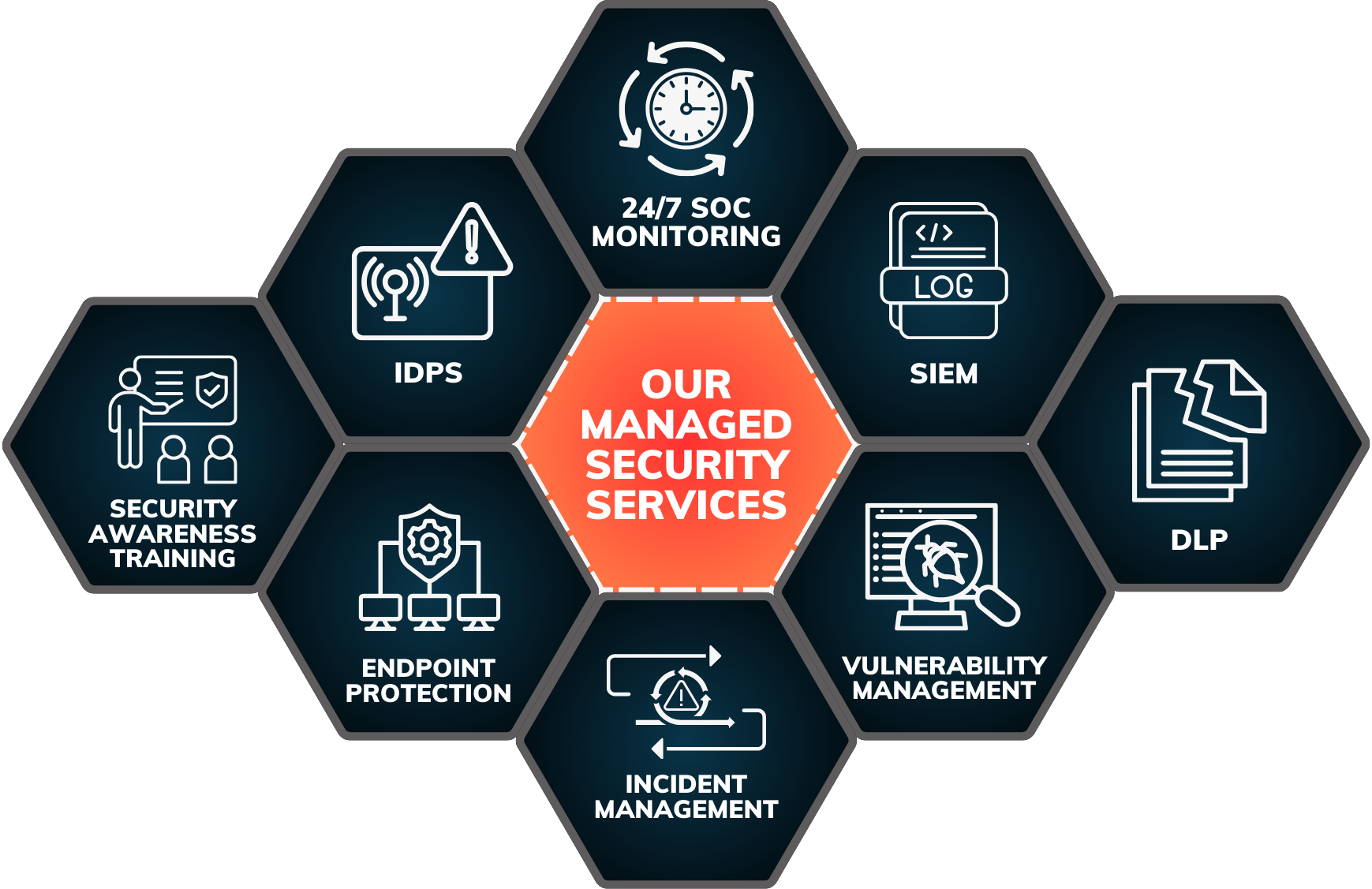
Our Managed Security Services Include
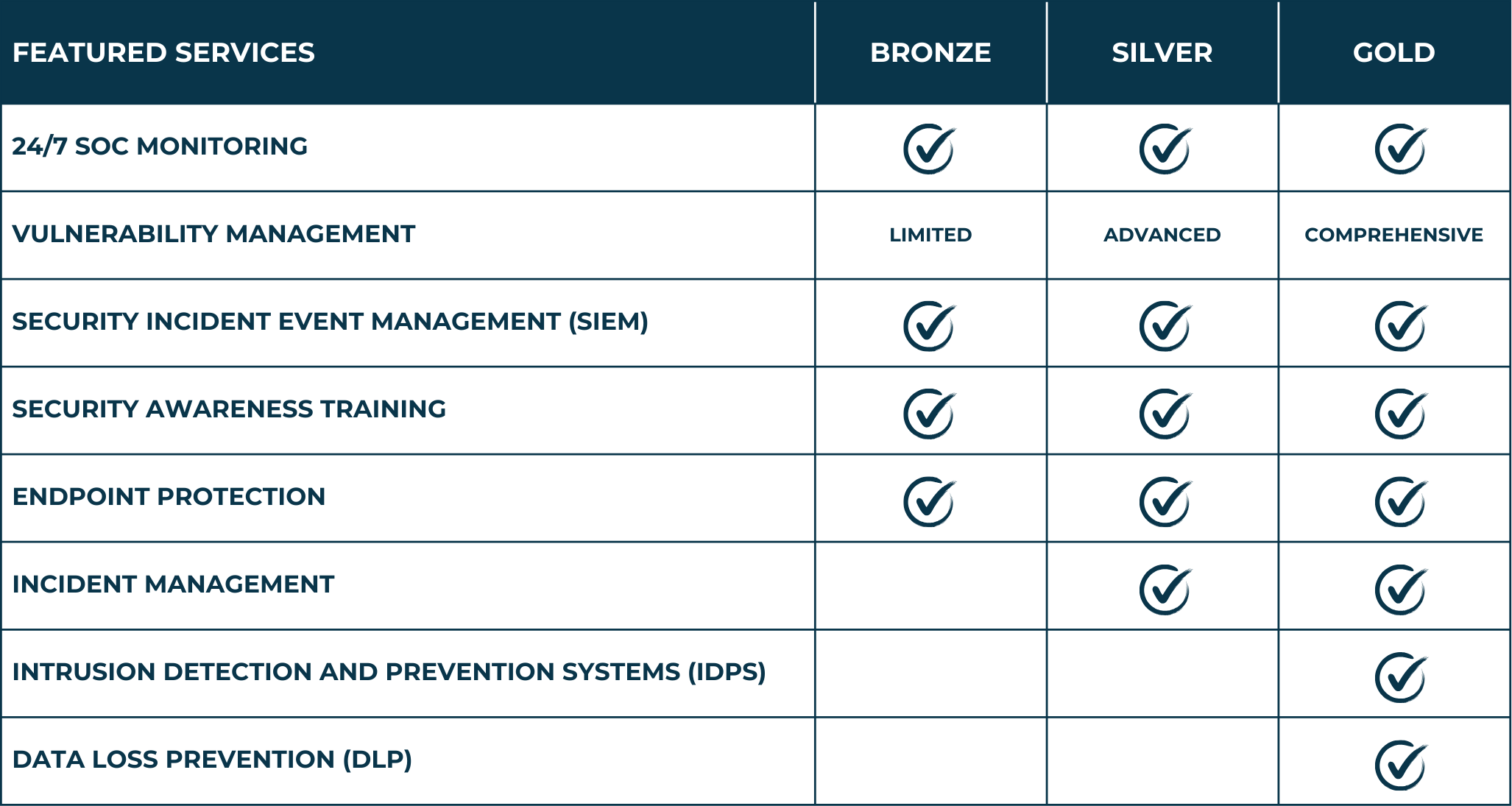
Our Managed Security Services Packages
How It Works
On-boarding
- Initial assessment and setup of monitoring tools.
Monitoring
- Continuous oversight of your network, systems, and data.
Reporting
- Regular reports on your security status and any incidents addressed.
Found your package?
How It’s Important
24/7 Security Monitoring and Incident Response
- Round-the-clock Protection: Our dedicated team provides 24/7 monitoring of your systems, ensuring constant vigilance against cyber threats.
- Rapid Incident Response: Immediate action is taken in response to security incidents, mitigating risks and minimizing disruption to your business operations.
- Proactive Security Measures: Implementing proactive security measures to prevent potential threats from escalating into serious incidents.
Vulnerability Management
- Identifying Security Weaknesses: Conducting comprehensive assessments to identify vulnerabilities within your systems and networks.
- Proactive Security Measures: Implementing proactive security measures to address identified vulnerabilities and strengthen your overall security posture.
- Continuous Testing: Regularly conducting vulnerability assessments and penetration tests to ensure ongoing protection against evolving threats.
Security Incident and Event Management (SIEM)
- Real-time Threat Detection: Utilizing advanced SIEM technologies to monitor and analyze security events in real-time.
- Immediate Response: Our expert team swiftly responds to security incidents, minimizing their impact on your business operations.
- Continuous Improvement: Constantly refining our SIEM systems and processes to stay ahead of emerging threats and enhance threat detection capabilities.
Dedicated Security Operations Center (SOC)
- Centralized Security Oversight: Operating a dedicated SOC staffed with experienced security professionals to oversee your organization’s security posture.
- Continuous Monitoring: Our SOC team continuously monitors your systems for security incidents and anomalies, ensuring rapid response and mitigation.
- Threat Intelligence Integration: Leveraging threat intelligence feeds to stay informed about the latest cyber threats and trends, enhancing our ability to detect and respond to emerging risks.
Threat Hunting
- Proactive Threat Detection: Actively searching for and identifying potential security threats that may go unnoticed by traditional security measures.
- Advanced Threat Detection Techniques: Utilizing advanced analytics and investigative techniques to uncover hidden threats and suspicious activities within your network.
- Immediate Action: Once threats are identified, our team takes immediate action to neutralize them and prevent further harm to your organization.
